I have clients, friends, and family who have been hacked or scammed and lost as much as tens of thousands of dollars and scores of hours of time to repair the damage done. This includes crap like calling vendors, banks, and law enforcement agencies and dealing with sleepless nights and lost data.
Therefore, I’d like to devote time here - and in future episodes - to help all of you understand the creative ways that malicious hackers use to part you with your money, time, belongings, and sanity.
I also get hit by attempts to bribe, confuse, or hack me. But unlike most people, I collect evidence and categorize them. Then, I can share them with you. That way, you can know what to look for and either avoid or stop the attempts cold.
Approach #1: Ransomware Threats
Ransomware, as its name implies, is the practice of demanding a financial ransom for a variety of real or imagined reasons:
Getting back a company’s critical data
Not publishing certain sensitive data including compromising photos
Locking computers down, sometimes with an alarming graphic on-screen
While most corporations invest substantial funds to establish digital firewalls to prevent hacks, it’s usually not enough. Then, they’re sometimes forced to pay huge ransoms - sometimes $5 million or more - to get back control of their businesses.
The reason so many high-level hacks are successful is that they use something called “social engineering”, the act of tricking company employees with requests that look legitimate but are not. This recently happened to both Apple and Meta (hat-tip to Charles Yaker for this link).
If business leaders need to train their employees on how to prevent these kinds of hacks, the doubly same is true for us individuals. So let’s check out a few of the most common kinds of tricks that hackers like to use.
Email
Email is hugely popular with malicious hackers and it’s easy to see why: anyone can write a threatening email, it’s dirt cheap to purchase tens of thousands of email addresses, and it only takes a few people to fall for the scam in order for the financial payoff to be huge.
Although most email applications have decent spam filtering, it’s not enough. Therefore, follow these four rules when it comes to avoiding scams and hacks:
Don’t open emails unless you know the individual or the company that sent them.
Once you’ve confirmed an email is safe to open, don’t click any links unless you first confirm that it’s safe. Do that by using one of these, two great tools: ScanUrl or PhishTank.
Never download any file or installer from any email. Yes, that’s strict, but it’s safe. The exception: if you know the senders, have confirmed their email addresses are correct and you’ve been expecting an attachment. If not, most email apps will offer a way to “quick view” an attachment without downloading it so you can view it online.
When in doubt, delete it. There will come a time when an email looks legit and you’ll reaaaallllly want to open it… but your Spidey Sense will be tingling. Please: resist that temptation. Trust your Spidey Sense and delete the email.
As these emails are designed to scare the shit out of you, don’t fall into your fear! Take a breath and then remember this: any reputable bank, government agency, or creditor will get in touch with you repeatedly. More importantly, they’ll usually start by sending you a letter via snail mail, not an email that asks you to act immediately.
When Shit Gets Creative
I mention fear because malicious hackers don’t actually need to infect your computer. Sometimes, they can infect your mind and do as much damage. Such was the case earlier this week when I got the following email:
The idiot went on to demand $1200 paid through Bitcoin to his digital wallet or else he’d blah, blah, blah, and then I’d suffer blah, blah, blah.
Now look: on its surface, this probably seems like a scary letter to some of you. I get that. However… you need to take a breath. Then use your tools. My Spidey Sense was telling me this was a scam. And so, after I took a few minutes to confirm my suspicions, I sent the following response:
Now, let me explain why I trusted my Spidey Sense:
First, the wording of this email was so general that it could have been sent to anyone. In fact, I KNOW that was the case because a few days later, I got the very same email sent to another email alias that I use! Sadly, I’m sure some of the targets paid the ransom out of fear, so here’s a tip: if the threatening email offers no specifics, report it, then delete it. For example, did the individual identify the make & model of your router? How about identifying which computers or smartphones you have? How about actually using your first and last name in the friggin’ email?!? See what I mean? None of that stuff was in this joker’s email.
Second, no one but me (and, perhaps, the FBI if this recent report from the Director of National Intelligence is correct) has access to any of my critical accounts. That’s because all of those are double-secured with two-factor authentication, or “2FA”. This technology is 100% free and something I recommend and covered in-depth back in Episode 36. I encourage you to start using 2FA immediately.
Third, both of my wireless routers are privacy & security-minded devices that I detailed and recommended to you back in Episode 40. Both are protected by user names and passwords which I change regularly. Both devices also keep logs which I checked to confirm that there was no unusual activity.
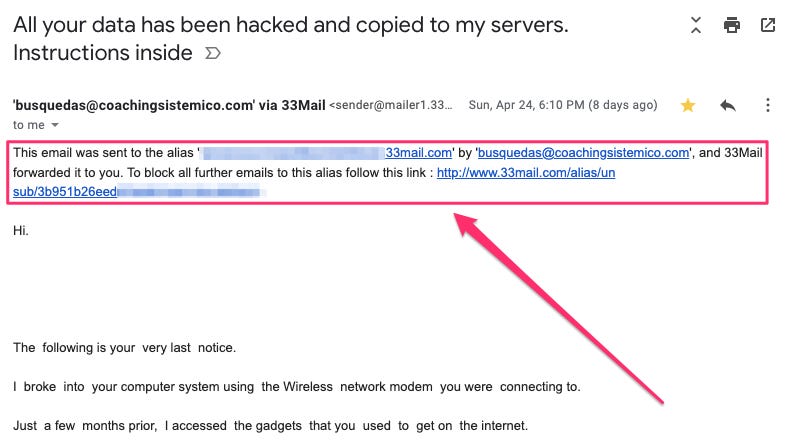
I’d like to share another tool that not only helped me confirm my Spidey Sense was accurate but also allowed me to eliminate any further communication from the idiots who tried to scam me. Take a look at the email I received. In particular, the top part:
I’ve used 33mail (affiliate link here) for years because it’s cheap and very effective at ending spam. I’ve actually recommended it multiple times: in Episode #3 and in Episode #23. The benefits are amazing:
When I create and use 33mail aliases, all emails sent to those aliases are forwarded to my actual email address through the company’s servers. That means… strangers don’t know my real email address.
When I reply to a forwarded email from 33mail, the company routes the reply through their servers. That way, my responses appear to come from my 33mail email aliases.
As you can see: EVERY forwarded email from 33mail comes with a header at the top with a link to INSTANTLY block that alias… and anyone who might wish to contact me using it. 🙌🏼
In practice, here’s what it looks like when I use it. You’ll note that I use the NAME of the website or service in my 33mail email alias. That way, I know which websites are responsible for losing, sharing, or selling my contact information:
Approach #2: Sales Threats
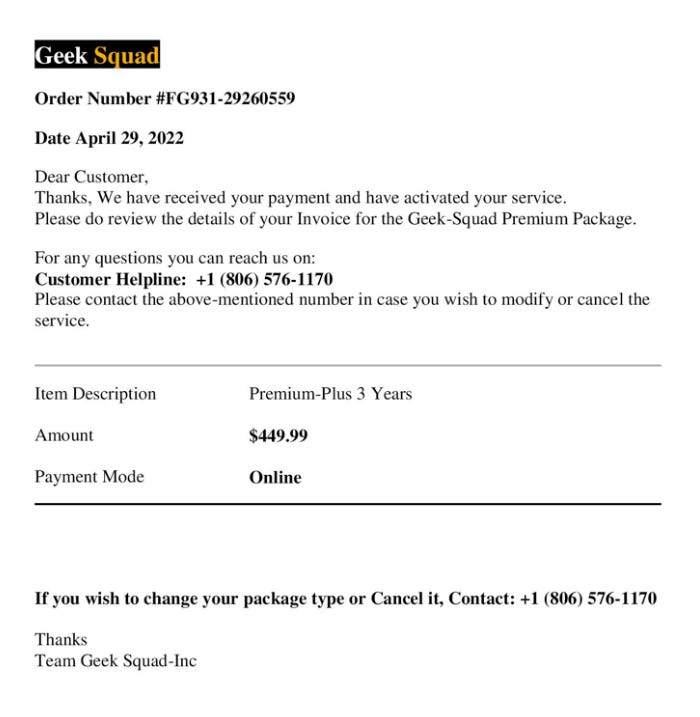
Here’s another email I got recently. Hmm… it looks like I bought something from BestBuy/GeekSquad, so that’s exciting!
The bad news? I didn’t actually purchase anything from Best Buy, so this is most likely a scam. Still, maybe they intended the email for another David Koff. As my Spidey Sense is tingling, let’s investigate further:
Check the return email address in the red rectangle. It’s not a Geek Squad or Best Buy email address. It’s a Gmail address. Strike one.
I did a quick view on the attachment (no downloads, remember?) and saw the following. I confirmed the phone number shown isn’t the number on the Geek Squad webpage. Strike two.
I called the number in question (from one of my Google Voice numbers, not from my cell), and a man with an Indian accent answered, not mentioning the name of the company. Strike three.
You’re out!
I have nothing against India, but every social security scam phone call I’ve received over the past five years features someone with that regional accent. I’m not imagining it either: in February of 2022, the U.S. Justice Department indicted bogus call centers in India.
Bonus Note: the link above to the U.S. Justice Department website also has excellent tools and tips for dealing with scam Social Security calls including these gems:
So remember: take a breath. Keep a level head. Hang up the phone if someone asks you act immediately. And never provide any critical data (bank account info, social security number, address, date of birth) to anyone who doesn’t first provide you with their information, their agency or company name, and the SPECIFICS about your problem.
Use the tools I’ve provided. Let me know how it goes. And as always… Surf safe.
And that’s a wrap for today’s episode, everyone. Thanks again to my free and paid subscribers for supporting independent technology journalism. I also thank you, in advance, for using the link below to share Tech Talk with your friends, family, and colleagues.
Popular Past Issues:
Which secure routers to purchase and WHY.
My 2021 recommendations on the best VPN providers.
My favorite, free tool to keep email addresses private.
A crash course on keeping your devices updated.
Product Recommendations
These are the devices and services that I personally use. I pay for everything you see listed here. I made these choices after much research and recommendations from tech industry colleagues.
The online backup software I use: iDrive (affiliate link)
The VPN software that I use: Nord VPN (affiliate link)
The email anonymizer that I use: 33Mail (affiliate link)
The secure router I use at my office: Gryphon (affiliate link)
The secure router I use at my home: Synology (affiliate link)
The service I use to block spam calls/texts: Uncall (affiliate link)
Transparency Statement
Some of the products and services I recommend pay me a small commission if you decide to purchase them. Making purchases based on my recommendations never costs you extra. In fact, it can sometimes save you money because I get access to certain discounts which aren’t available to the general public.
It’s a win-win: you save money and help me earn an additional salary from my writing. Thank you, in advance, for that. It’s an easy way for anyone to support my work, research, and expertise. Affiliate links will be shown like this → (affiliate link) to make them easy to identify.
In case you’re curious:
I’ve purchased, owned, tested, and/or deeply researched every single thing I recommend.
I’m never paid to sell software or hardware to you.
I retain 100% editorial control over everything I write.
The companies, products, or services that I recommend don’t know that I’m going to mention them.